Trezor Bridge: Secure and Seamless Connection for Your Trezor Hardware Wallet
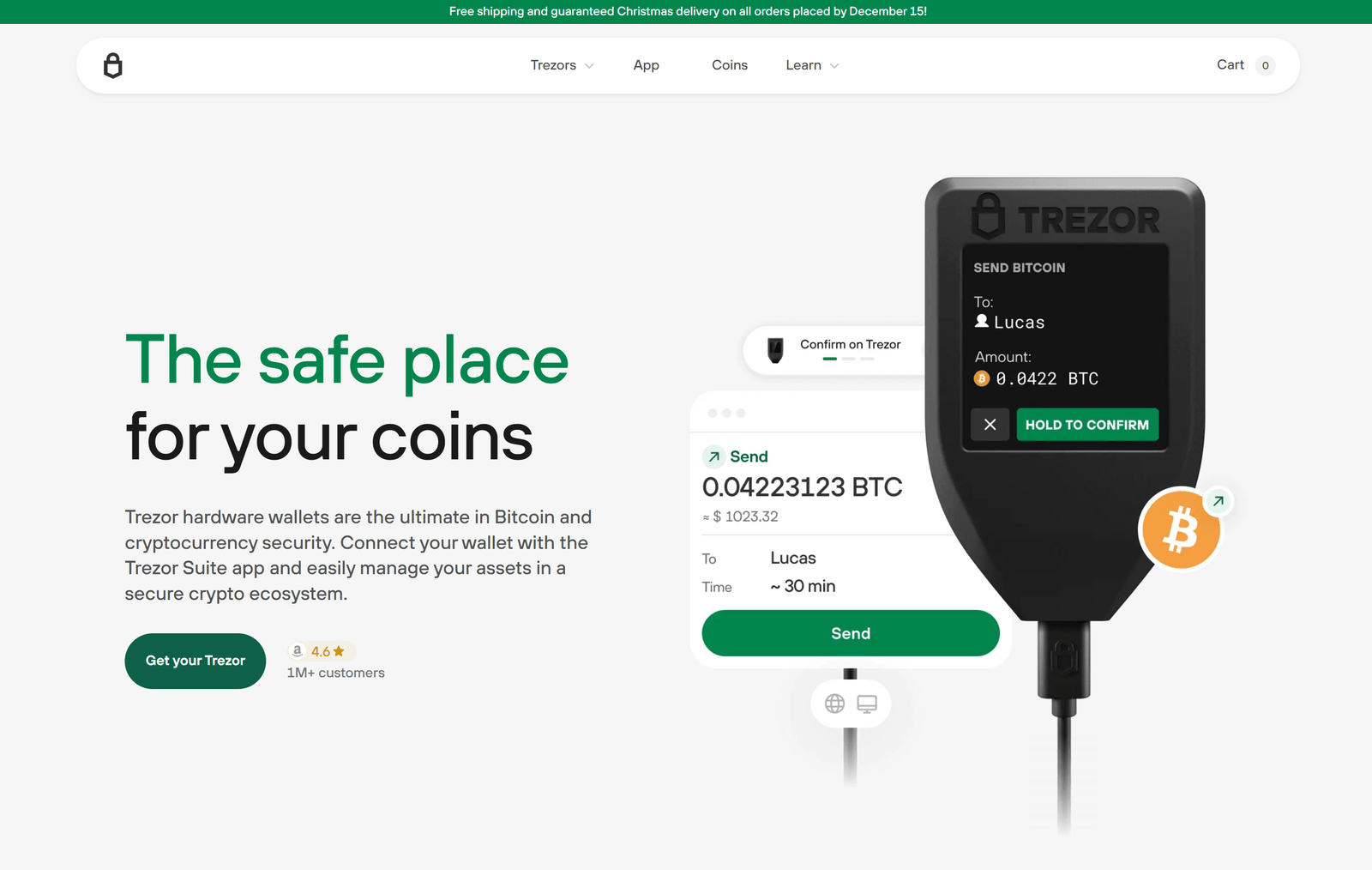
Trezor Bridge is an indispensable software that acts as a secure communication link between your Trezor hardware wallet and your computer. It works silently in the background to ensure your browser or desktop applications can properly detect and interact with your Trezor device. Since hardware wallets operate in isolated environments to protect private keys, they cannot directly communicate with browser-based cryptocurrency tools. Trezor Bridge fills this gap by creating an encrypted communication tunnel that connects your Trezor wallet with web applications securely.
One of the key advantages of Trezor Bridge is enhanced security. All sensitive operations, including transaction signing, happen directly on the Trezor device itself, meaning your private keys never leave the hardware wallet. This keeps them safe from potential malware or phishing attacks on your computer or browser. It supports modern browsers like Chrome, Firefox, and Edge without needing extra extensions, simplifying the user experience.
Another benefit is its seamless integration and automatic operation. Once installed, Trezor Bridge runs quietly at startup, automatically detecting when your Trezor device is connected and establishing an encrypted link without requiring manual intervention. This ease of use makes managing cryptocurrency accessible even for less technical users.
Additionally, Trezor Bridge overcomes technical barriers with USB communication in browsers, providing consistent compatibility across platforms including Windows, macOS, and Linux. It also offers robust diagnostic tools for troubleshooting connection issues.
In summary, Trezor Bridge is essential for the smooth and secure management of your cryptocurrency. It bridges the secure offline environment of your Trezor hardware wallet with the dynamic online crypto ecosystem, protecting your digital assets while keeping interactions user-friendly.
Advantages of Trezor Bridge:
Ensures private keys stay securely on the hardware device
Provides encrypted communication with browsers and apps
Supports major browsers without additional extensions
Runs automatically and silently in the background
Enhances user experience with easy plug-and-play functionality
Cross-platform compatibility and robust troubleshooting tools